Reversing ELF | TryHackMe Writeup
Link to room: https://tryhackme.com/room/reverselfiles
This room allows you to test your skills at reverse engineering ELF binaries giving you 8 fun challenges to solve in total. The setup is fairly simple as you just need a Linux machine, some reverse engineering tools of your choice and basic RE knowledge. You’ll also need to download and grant each binary execute permissions. I had a lot of fun solving these and I hope you do too :D

Crackme1:

The first binary is very straightforward and doesn’t require any effort as it simply tests your computer skills. Execute this binary without any arguments and you’ll get your first flag.
Crackme2


The second task is where the challenge begins. To solve this, I went with Radare 2 as this is what I usually use to approach simple binaries. Here I opened the file with r2 <name_of_file>. I then analyze the binary with aaa, list all functions with afl and finally open the main function with pdf @main.


Upon opening the main function, we can very clearly see the string that is used as the secret password. We can then take that string and pass it as the first argument to the binary and we get our flag.
Crackme3


The third challenge is when things start to get more complicated which is when I switched over to Ghidra as it’s much nicer to navigate, it offers a decompile view and because I was working on improving my Ghidra skills. Here we see a string compare being used against a long string which looks to be encoded which led me to take a guess at Base64 and to my luck decoding it turned out to be right.
Crackme4



This binary also uses a string compare however decomiling it isn’t of much use as it appears to calculate the flag with a function that doesn’t reveal much. A simpler way would be to get the program up and running with gdb so we can inspect the registers before the string compare is executed. We open the binary with gdb, list all the functions, find the address of string compare and then set a breakpoint to stop the program when the function is called.


Checking the registers reveals a few values being held so we first check rax as that’s one of the most important registers. By inspecting the hexadecimal value stored at that memory location and converting it to a string, we get the flag.
Crackme5

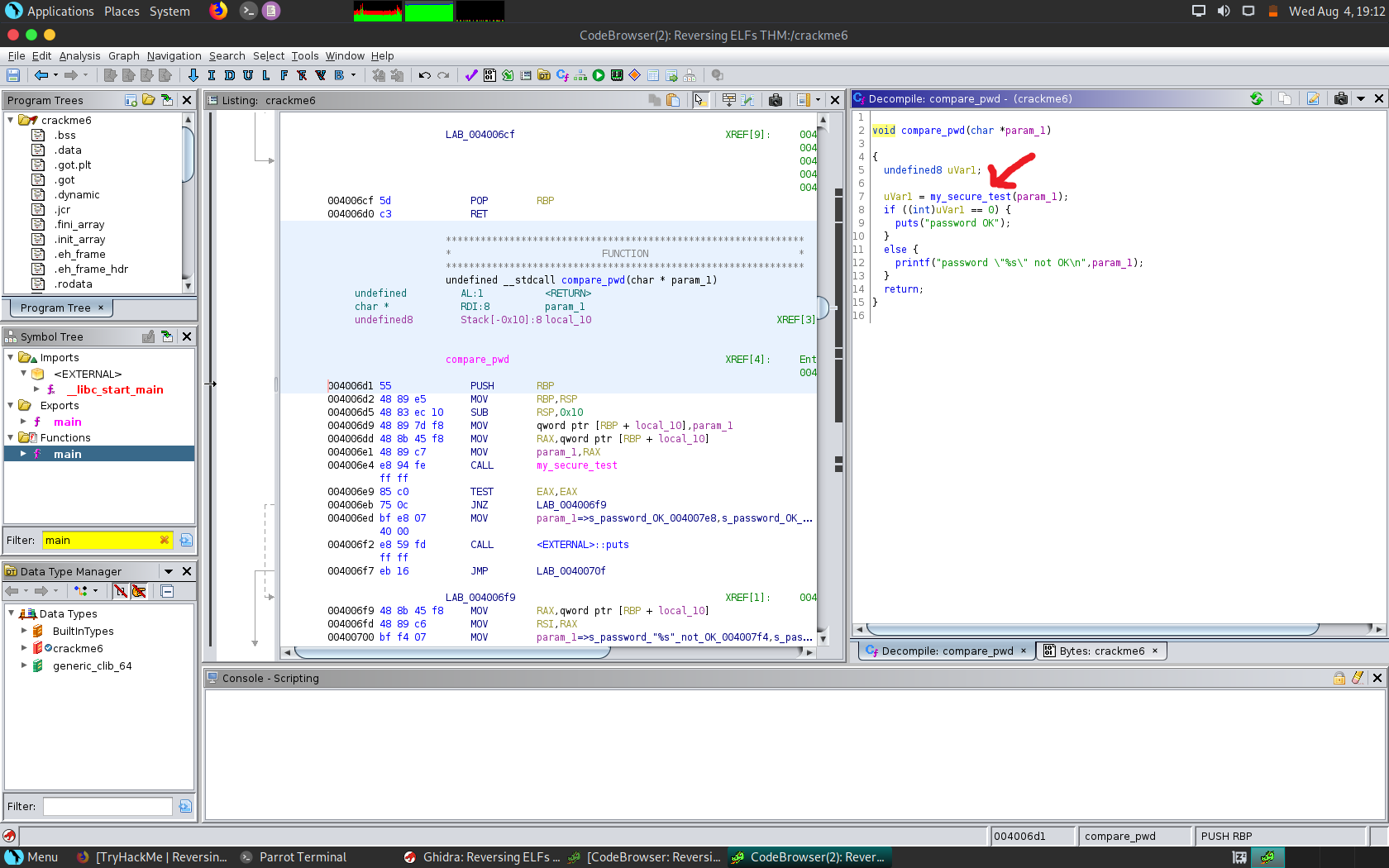
Crackme5 takes us back to Ghidra now that the binary can be statically analysed. We begin exploring the main function however this sends us on a little journey to backtrack where the actual password is stored. First we enter compare_pwd which then seems to use my_secure_test to return true or false which will advance the program further which shows us that this is where the main check most likely takes place.


It seems we were correct as this function contains a LOT of conditional statements which check a set of letters in the first argument that we provide to the program along with a hexadecimal value under each one which equates to true which is then used to return the state of the password check. We can then take all the values and stitch them together in order to get the flag.
Crackme7

This binary is more complicated than the others which led me to first checking each input by running the binary however this didn’t reveal anything.
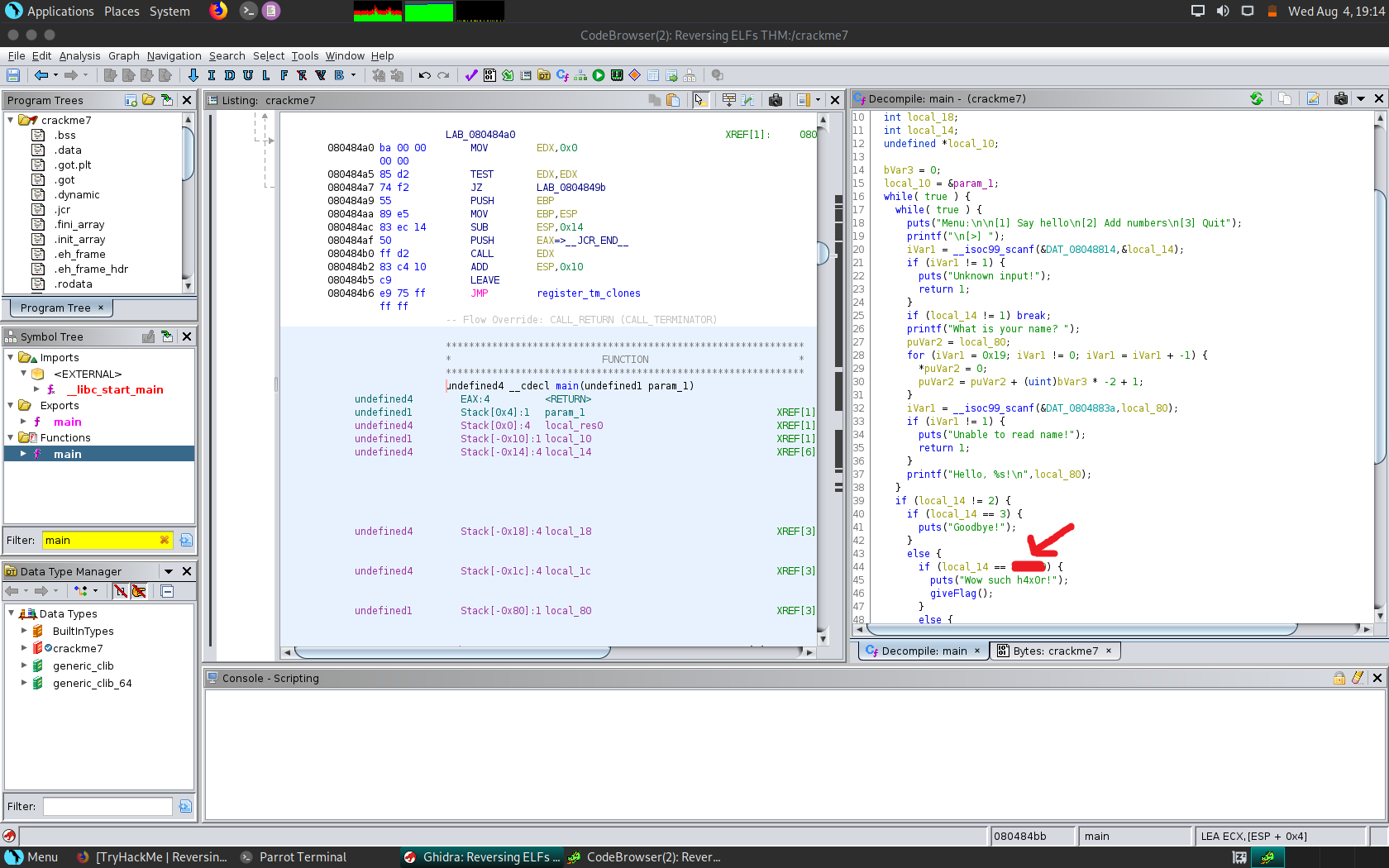

As I was looking through the decompile view, I noticed a pattern which revealed to me all the different paths the binary can take with one standing out as it contained an interesting message. To reach that we need to supply a special value which we can uncover by right clicking it and seeing all the different representations of it which Ghidra really nicely presents.

I can see that it doesn’t seem to be a string so I passed it as a decimal as that made the most sense and I get the flag.
Crackme8


The final binary turned out to be easier than I expected once I took a closer look at the decompiled code. The program is unlocked once an int value is equal to the hardcoded value. The atoi function above it converts our program argument string and changes it to an int value which led me to do the same trick from the previous task.
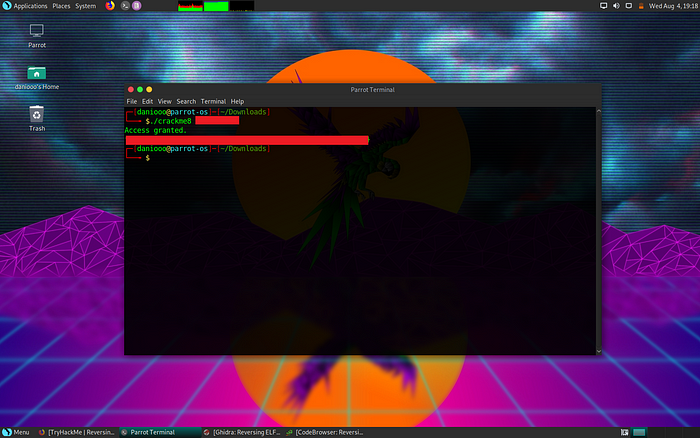
We pass the value in as the first argument for the program and get the final flag :D
This room was quite fun to complete since the binaries were interesting to explore and they weren’t too easy nor difficult. I got to practise my debugging and Ghidra skills along with learning more about the insides of ELF binaries.

